Statistical Ineffective Fault Attacks (SIFA) are a fault attack technique for implementations of symmetric cryptography. SIFA's main advantage is that it can circumvent many typical countermeasures, including fault detection and masking.
This website provides some interactive examples to understand SIFA in more depth.
Idea
SIFA combines ideas of Statistical Fault Attacks (SFA) and Ineffective Fault Attacks (IFA). The attacker first collects ciphertexts by encrypting some plaintexts and inducing a fault in every computation, somewhere near the beginning or end. Then, they guess part of to the key to recover an intermediate value near the fault location. Like SFA, the correct key candidate is recognized based on the distribution of values in this location: for the wrong keys, the distribution is roughly uniform; for the right key, the distribution is that caused by the fault, which is ideally very non-uniform. Like IFA, SIFA only uses faulted computations that lead to correct ciphertexts, i.e., where the fault was induced but ineffective, in order to circumvent countermeasures such as fault detection.
Works on Fault Countermeasures
Because SIFA only uses ineffective fault inductions, it works even in the presence of countermeasures like fault detection, where an attacker can only get ciphertexts if the fault had no effect on the output. For example, if the fault is a bit-stuck-at-0 fault, the fault is ineffective if the target bit was already 0; thus, this target bit will be 0 if we only look at ineffective samples. This works not only with such biased faults, but also with bitflip faults – if the bitflip fault affects wires within an S-box, while the attacker analyses the S-box output value for key-recovery.
To understand the effect of this output filter when a bitflip is applied inside an S-box, check our Demo: Ascon S-box. Here you can examine the implementation of 5-bit S-box used in Ascon. If you enter some input and pressing the play button, it will calculate the correct result. The input can either be fixed to 0, 1, or marked with an asterisk * to allow both values. By hovering over the computation graph, it is possible to induce faults on certain positions and see how the result changes. Below the circuit, you can investigate the main parameters that influence the efficiency of an attack based on this fault: the capacity and the ineffectivity rate. The graphs underneath show the input and output distributions of values among only the ineffective cases.
Works on Masked implementations
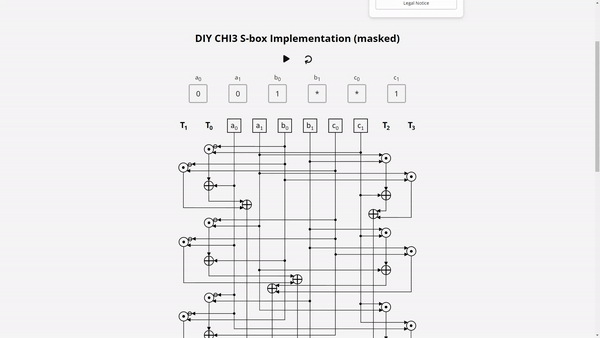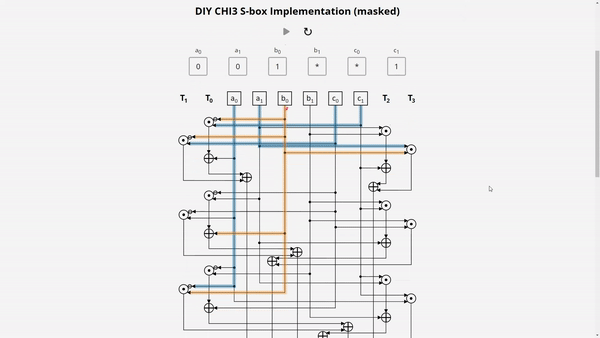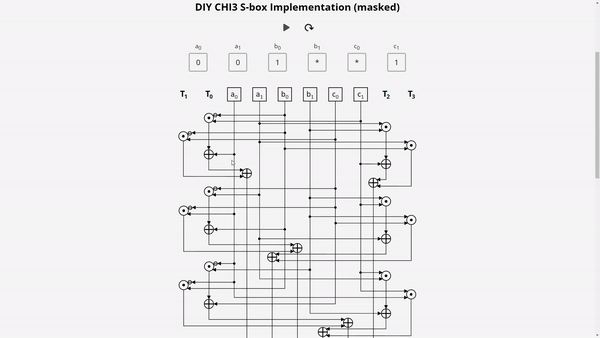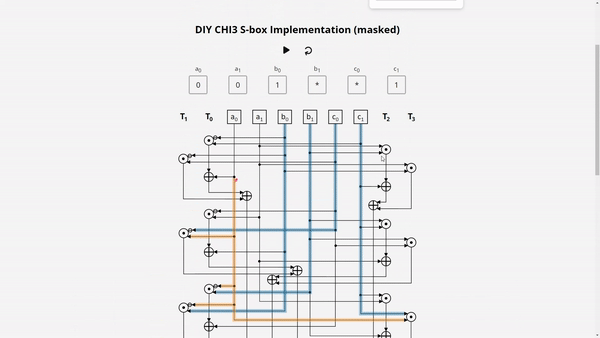
In a masked implementation, learning values of an individual share is useless for the attacker, as it is independent of the native bit values. With SIFA, an attacker can learn the values of multiple shares based on single fault. To see how this works, check our Demo: Masked χ3 S-box. Here you can examine a simplified masked implementation of the 3-bit χ3 S-box, which is used for example in Xoodyak.
Key Recovery
For an example of how key recovery with SIFA works for AES, check our Demo: AES Key Recovery.
References
Christoph Dobraunig, Maria Eichlseder, Thomas Korak, Stefan Mangard, Florian Mendel, and Robert Primas. SIFA: Exploiting Ineffective Fault Inductions on Symmetric Cryptography. In: IACR Trans. Cryptogr. Hardw. Embed. Syst. 2018.3 (2018), pp. 547-572.https://doi.org/10.13154/tches.v2018.i3.547-572.
Christoph Dobraunig, Maria Eichlseder, Hannes Groß, Stefan Mangard, Florian Mendel, and Robert Primas. Statistical Ineffective Fault Attacks on Masked AES with Fault Countermeasures. In: Lecture Notes in Computer Science 11273 (2018). https://doi.org/10.1007/978-3-030-03329-3_11.
Joan Daemen, Christoph Dobraunig, Maria Eichlseder, Hannes Groß, Florian Mendel, and Robert Primas. Protecting against Statistical Ineffective Fault Attacks. In: IACR Trans. Cryptol. Hardw. Embed. Syst. 2020.3 (2020), pp. 508-543. https://doi.org/10.13154/tches.v2020.i3.508-543.