Demo: AES key recovery using SIFA
Scroll Down
This page represents an AES key recovery
on a 10 round unprotected AES implementation
applying Statistical Ineffective Fault Attack.
Wide-Trail Design Strategy.
The state of this AES-128 implementation is represented by a
4x4 bytes grid.
The AES implementation consists of four different round functions:
SubBytes (SB)
Bytes are transformed by an
invertible S-box.
Same S-box (lookup table) for the whole cipher. It is based on multiplicative inverse in GF(28).
Bytes are transformed by an
invertible S-box.
Same S-box (lookup table) for the whole cipher. It is based on multiplicative inverse in GF(28).
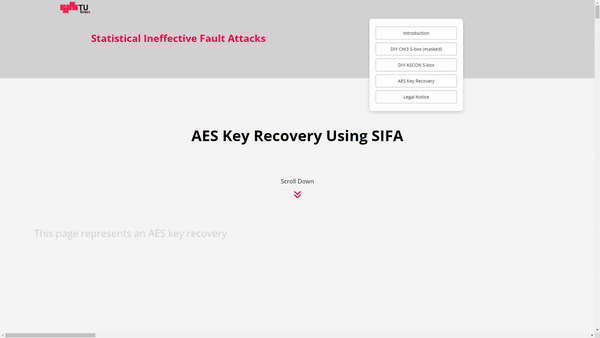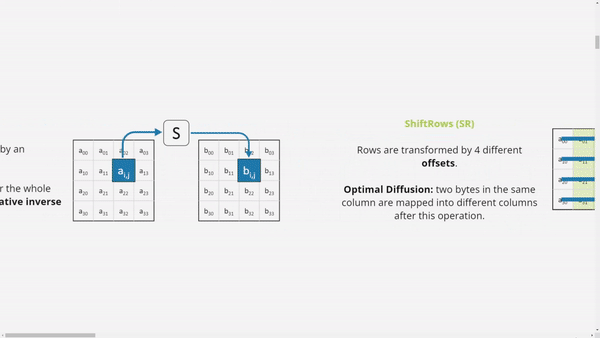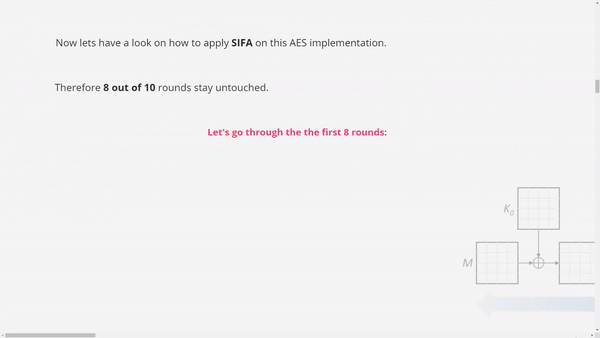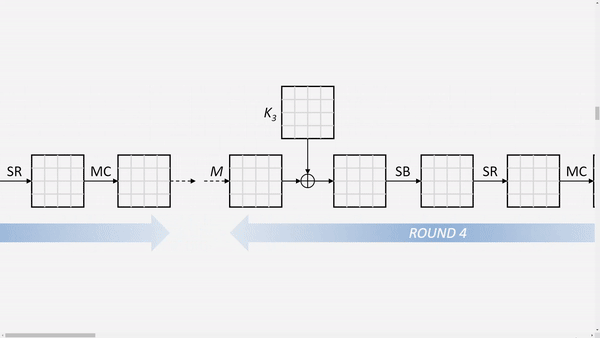
ShiftRows (SR)
Rows are transformed by 4 different
offsets.
Optimal Diffusion: two bytes in the same column are mapped into different columns after this operation.
Rows are transformed by 4 different
offsets.
Optimal Diffusion: two bytes in the same column are mapped into different columns after this operation.
MixColumns (MC)
Columns are transformed by 4 x 4 matrix over GF(28).
Linear function with Branch number B = 5. Together with ShiftRows, high diffusion over multiple rounds.
Columns are transformed by 4 x 4 matrix over GF(28).
Linear function with Branch number B = 5. Together with ShiftRows, high diffusion over multiple rounds.
AddRoundKey (AR)
One part of the key for each of the rounds.
This makes the round function key-dependent.
One part of the key for each of the rounds.
This makes the round function key-dependent.
Now lets have a look on how to apply SIFA on this AES implementation.
Therefore 8 out of 10 rounds stay untouched.
Let's go through the the first 8 rounds:
Now, one byte of the 4 x 4 grid is chosen.
In the SubBytes step, some fault is induced into one S-box implementation.
Providing enough plaintext values,
this leads to a non-uniform distribution within this byte.
This propagates through the last rounds:
Notice that the last round ommits the MixColumns step.
For simplicity, the important bytes are marked after the 10th round.
The last round is calcualted back until we end before the MixColumns step of round 9.
The marked bytes are now examined.
If we observe a distribution with very small distance to the uniform distribution
the key guess was incorrect!
If we observe a distribution with very small distance to the uniform distribution
the key guess was incorrect!
The marked bytes are now examined.
If we observe a distribution with very big distance to the uniform distribution
the key guess was correct!
If we observe a distribution with very big distance to the uniform distribution
the key guess was correct!
But wait! Guessing 8 bytes means to guess 264.
We try to ignore K9 in the back calculation as this is only a variant of the key.
We again observe a distribution with very big distance to the uniform distribution and
the key guess was correct!
We try to ignore K9 in the back calculation as this is only a variant of the key.
We again observe a distribution with very big distance to the uniform distribution and
the key guess was correct!
This is how to recover the key for some AES-128 implementation using SIFA!